ST-ONE
micro-embedded STM32!
 Русский
Русский
 English
English
Micro-platform for electronic devices based
on the ARM processor
Play 

ST-ONE has a simple and flexible configuration system. The configuration file has a standard INI format. Variables have meaningful names and are specified by the options described in this document. The configuration of the bootloader and firmware is in the FIRMWARE.INI file located in the root of the USB disk of the bootloader.
The configuration file is located in the root of the emulated disk and is named FIRMWARE.INI. The directives set in this file will help you to configure the bootloader precisely and allow you to manage the process of downloading the main firmware using, among other things, licensing.
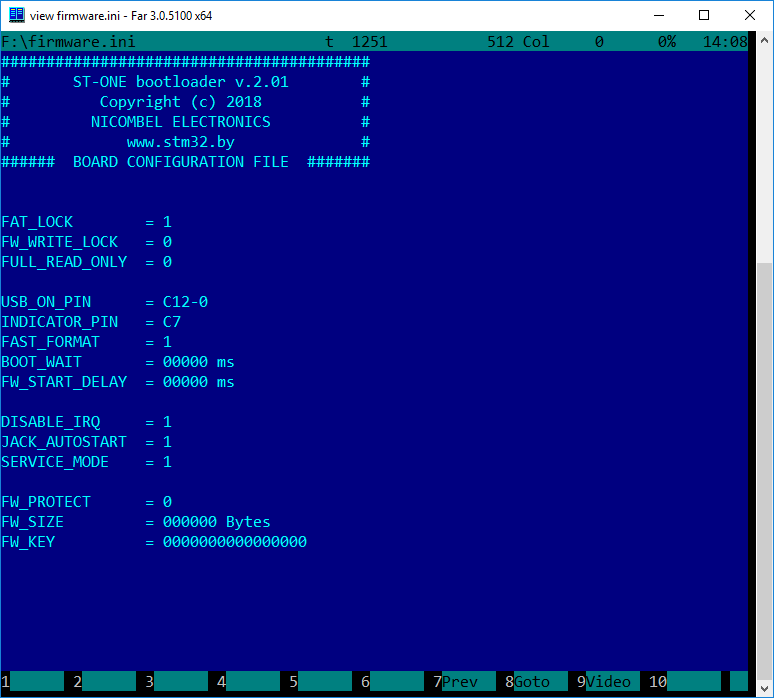
According to the agreement, Latin characters in UPPER case are used when working with the configuration file. The size of the file cannot exceed 512 bytes. This size is enough to set all the necessary parameters. By doing so is excluded more complex processing of file at system startup, which allowed to reduce the size of the bootloader code to only 32 KB.
FIRMWARE.INI has rich capabilities for configuring the system. The list of main directives is in the table below:
| Directive | Value | Description |
|---|---|---|
| FAT_LOCK | 1 / 0 | Locks of FAT table of files allocation |
| FW_WRITE_LOCK | 1 / 0 | Inhibition of write and delete the firmware. Applies the protection only on the area of storage of the firmware itself and its modules (if any) |
| FULL_READ_ONLY | 1 / 0 | Puts the device in a full READONLY mode. Therefore, you cannot reset this flag back - only through system formatting |
| USB_ON_PIN | [PIN][NUM]-[1 / 0] | Complex composite parameter. Allows you to set a PIN for connecting the chip to USB. The ST-ONE brand board uses a special electronic key to connect the USB - it is controlled by this software parameter. |
| INDICATOR_PIN | [PIN][NUM] | Led indicator of bootloader status |
| FAST_FORMAT | 1 / 0 | System formatting. If 1 is given - it’s a fast format, 0 is a full format of the crystal |
| BOOT_WAIT | ms | Waiting for the input of hardware command of entry to the loader in milliseconds. Timeout of Vcc waiting on PIN 1. If Vcc is not present (0) - the control is transferred to the main program [taking into account FW_START_DELAY] |
| FW_START_DELAY | ms | Delay in milliseconds before the start of the main firmware |
| DISABLE_IRQ | 1 / 0 | Disables interrupts at the time of transfer of control to the main program. 1-block the interrupts, 0- allow interrupts |
| FW_PROTECT | 1 / 0 | Protect firmware from reading. With installation of this option, it will be impossible to change or read the crystal! This option also includes a hardware protection. Attention! Removal of such protection is possible only by a special JACK-subroutine or by complete erasing of the whole crystal |
| FW_SIZE | bytes | The size of firmware in bytes. Required for correct calculation of MD5 firmware |
| FW_KEY | string | The key for hardware decoding and installation of the main firmware. Used for licensing and protection of spread SOFTWARE. |
The number and list of options may vary depending on the software and chip version.
For a better understanding of options operation, it is recommended to learn the General principles of operation of FAT12 / FAT16 file systems. Let us consider in more detail each of the directives and its area of application:
The Directive is required for enforced lock of file allocation table. By default, the option is always enabled and concerns only and directly the FAT table itself. This is done in order to exclude the impact of the operating system of the computer, where to the device is connected, on FAT and its content. For example, Windows can create business accounts, create hidden folders and files. Third-party SOFTWARE can also create certain tags or hidden files on USB-media. If the file allocation table is locked, the file structure is guaranteed to remain unchanged. That is, the number of files and their virtual size will be the same as after system formatting. Efficient use of the option is achieved in conjunction with FW_WRITE_LOCK. At the same time, the contents of the file space can be changed, as the operating system may decide that it has successfully updated FAT, more about this on.
The Directive is necessary to force the blocking of the FLASH-memory area which is marked under the main firmware and contains changeable data. Default is always 0 When you set this option to 1 and after restart of the device, the firmware file FIRMWARE.INI will be closed for editing. Together with the FAT_LOCK option, this will provide guaranteed protection of the firmware against accidental changes from the outside, as in case of regular access to the file system, so through the utilities of direct work with disk. At the same time, the set of these options is not a protection against unauthorized access (copying). You can read the code and all files of parameters. You can also easily remove this protection through FIRMWARE.INI, for example, to update firmware or write other firmware.
Forced switch of entire file system of the device into READONLY mode. Default is always 0. If you set this option to 1 - we will get the device read-only. This will lock the write to any sectors of the emulated disk, and the FIRMWARE.INI file will no longer be available for editing. Therefore, you can only remove this protection by formatting the system. This option ensures that the data on the device is as stable as possible, and the firmware will always run with guaranteed bootloader parameters. The Directive is not a protection against unauthorized access and provides unhindered access to the crystal memory for reading.
Complex composite parameter. It can take different values. Implemented for maximum flexibility of the solution, no matter on which Board and in which chip the loader will work. The essence of the parameter is to set the PIN and its status for USB activation. In the right solution for USB connection, there will always be an electronic key of software control of USB-bus switching with external devices. The role of the hardware key can be performed by the "digital transistor", as it is done, for example, on the ST-ONE brand Board. When low potential is applied to this key - USB bus will be connected to the controller and the device will be connected to the outside world. Thus, we get the ability to control the connection and disconnection of the device from the external electronics without breaking the interfaces (without removing the cables).
The value of the parameter is formed as follows: the port and the PIN of the USB power-on logic control are set, the status necessary for the activation of the electronic key is indicated through a hyphen. Thus, if we have the key hanging on the PIN12 of port C, and to activate it requires low potential, the value will look like: C12-0. If the key is hanging on port B, PIN7, and to enable the logic requires high potential - the value of the parameter will look like: B7-1.
Complex composite parameter. It can also take the value of the port and PIN-a. The indicator is used to display the status of the loader and the current operation. For example, if we have an indicator on port C and PIN7 - the value of the parameter will be C7.
It is used to determine the type of system formatting. Required to quickly reset the device to factory state. Fast formatting has the same mechanism as fast formatting in the operating system on the computer. The default is always 1. If you turn off the parameter to 0 - formatting will always be carried out in full. That is, everything from the MBR and file tables to the firmware space will be overwritten. Full formatting takes a few seconds longer time and ensure to remove all previous data. The parameter is dependent on the FW_PROTECT parameter When protection is turned on the formatting is impossible and return to initial state is only possible with the help of JACK-subroutine for reset or by full erasure of the code with subsequent reprogramming.
It is an option to specify the timeout in the period of which will be expected the hardware command of entry into the bootloader. It can be used in devices that require periodic updates or entry into the loader to perform service tasks. On bootloader activation PIN can be brought up a button or commutation circuit for activation of the bootloader by external event. This will allow more flexibility to use the final device without having to modify the electronic circuit. If the command for entry in bootloader has not arrived in the wait period the control will be transferred to the main microprogram.
Delay before starting the main firmware. This option is used to pause before the start. It can be useful when you want to complete any long-term transients after powering the device. The bootloader will wait for the set timeout and give control to the main firmware.
Lock out interrupts on the time JUMPs into the main firmware. The default is always 1. This means that the controller will perform the transition to the main firmware in complete silence (without interrupts). This imposes certain requirements on the underlying firmware. For example, when the main program starts, you must allow interrupts again. The value can be reset to 0. Then the transition to the main subroutine will be performed at your own risk, with the ability to call interrupts. If at the moment of transition the handler of some event is called, the system may hang. The device can be started with or without interrupts, depending on the situation and the configuration of the main firmware. The vast majority of starts are successful at any parameter value. The user can adjust this by increasing the guaranteed reliability of the device.
Protection of the device. This option can be used both separately and in conjunction with the license. Implements full protection of the device. If this option is activated, the device must be restarted. The protection will be installed. Then the indicator will show the success of the operation and the device should be de-energized. All the subsequent starts will be in protected mode. The user will still be able to activate the bootloader startup, but will not be able to read the main firmware program. Not be able to make changes to the files. This is necessary for copyright protection or in other situations where changing or reading the firmware is unallowable. When installing this protection, 2 protection modes will be activated: software and hardware. Software protection mode will ensure the correct operation of the device with the boot loader, through which it is no longer possible to extract the executable code of the main firmware program. Hardware mode will provide protection of the crystal at the hardware level. It will be impossible already to write or read anything from the controller. Even with the help of the programmator. The format command does not work in any form in this mode. Only the service mode is available if it is not disabled in the configuration files. Attention! When you run any JACK-subroutine on the protected chip the automatic erasure of the main firmware and bootloader will happen! If the service mode is available, then the device may return softly to its initial state: a working bootloader with an empty crystal to load firmware. If the service mode is not available-the device is completely locked and to return it to its initial state you will need a programmator, as well as a new bootloader. You will need to perform a complete erasure of the entire crystal and a repeated reprogramming.
Used to specify the size of the main firmware in bytes. This is necessary for correct calculation of MD5 - sum of the firmware dump. If this option is set, the file README.TXT will be able to see the firmware checksum, which will provide full control of the software integrity. Thus, checking the checksums-you can be sure that the executable code is written correctly, is not destroyed and is not modified. If the parameter is not set or is 0, the checksum is not calculated.
Used by the licensing mechanism. Through this parameter is passed the software protection key. Protected firmware can be distributed in the open access, including via the Internet. Only users of devices with ST-ONE bootloader will be able to use this firmware. The firmware is downloaded to the device in the usual way, then the license key is registered, the FW_PROTECT mode is set to 1 It is highly desirable at this step to set the firmware size to have the checksum of the firmware being installed. Then you need to restart the device. The firmware installation will begin. The event indicator will inform the user about its actions. Keys can be of different types. The firmware can be designed for a specific device with a specific ID, it can be installed only on the target device, or on any devices.
If the parameter is not specified or equal to 0, and if FW_PROTECT not equal to 1, the installation of the licensing firmware will not be performed.
